
3.10. Impacts of CS Electronic Documents¶
Time Estimate: 135 minutes
3.10.1. Introduction and Goals¶
|
Computing has transformed our lives in so many ways. Mobile computing, where we are constantly connected to others and to the world via our devices, is challenging us to develop new norms about privacy, security, rights, and other issues. Like any technology, mobile computing has both positive and negative impacts. We need to reflect on these impacts in general and on the impacts of the mobile apps we create. |
|

|
Learning Objectives: I will learn to
Language Objectives: I will be able to
|
3.10.2. Learning Activities¶
- Blown to Bits Chapter 3
- |
- Conversation Questions Template
- |
- Now That's Surprising! Template
- |
- Steganography Activity
Chapter Three: Ghosts in the Machine: Secrets and Surprises of Electronic Documents
Chapter Three of Blown to Bits describes how digital documents, including images and sounds, are represented by sequences of bits. Why do you think this chapter is called "Ghosts in the Machine"?
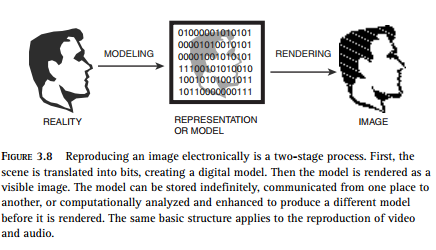
As you learned in the previous lesson and as shown in the this diagram, the first step in representing an image is to convert it into a sequence of bits. This is known as modeling. The model is an abstract representation of the original image.
Activity: Read Chapter Three (up to page 99) to discover what's hidden in electronic documents.
- Part 1: What You See Is Not What the Computer Knows - Read pg. 73 and 74 out loud as a class and discuss the word "redacted." Continue reading this section (up to pg. 80), using the Conversation Questions Template to write down a question about 3-4 ideas that were important, surprising, or thought provoking. In small groups, discuss your questions.
Metadata (data about data) is described and discussed on pg. 78-80. Here are a few additional things you should know about metadata:
- Metadata are used for finding, organizing, and managing information.
- Metadata can increase the effective use of data or data sets by providing additional information.
- Metadata allow data to be structured and organized.
- Part 2: Representation, Reality, and Illusion - Read pg. 80-94 and complete the Now That's Surprising Template. In small groups, discuss your notes.
- Part 3: Hiding Information in Images (pg. 95-99) is called steganography. First, answer the question below, then read the chapter pages as needed to help you complete this activity—you'll have an opportunity to hide your initials, or some 3-letter word, in an image. Try it, it's fun!
3.10.3. Summary¶
In this lesson, you learned how to:
3.10.4. Still Curious?¶
Printers sometimes add secret dots to documents when they're printed, very similar to steganography. In fact, the secret dots on a leaked, classified document were able to help the FBI identify a potential suspect. Read more in this article from the BBC.
3.10.5. Self Check¶
Vocabulary
Here is a table of the technical terms introduced in this lesson. Hover over the terms to review the definitions.
| algorithm
analog ASCII cloud computing cryptography |
digital
download lossless compression lossy compression megabyte |
megapixel
modeling OCR pixel raster |
render
spam steganography upload |
Check Your Understanding
Complete the following self-check exercises.
- Determining the likelihood that the photo is a picture of the sky
- Determining the likelihood that the photo was taken at a particular public event
- Determining the number of people that appear in the photo
- Determining the usability of the photo for projection onto a particular color background
Q-1: AP 2021 Sample Question: A digital photo file contains data representing the level of red, green, and blue for each pixel in the photo. The file also contains metadata that describe the date andgeographic location where the photo was taken. For which of the following goals would analyzing the metadata be more appropriate than analyzing the data?
3.10.6. Reflection: For Your Portfolio¶
Answer the following portfolio reflection questions as directed by your instructor. Questions are also available in this Google Doc where you may use File/Make a Copy to make your own editable copy.