
6.6. Cryptography Basics¶
Time Estimate: 90 minutes
6.6.1. Introduction and Goals¶
In the preceding lesson, you built a Caesar Cipher app and learned that cryptography means secret writing. It is the art and science of sending secret messages and it has been used by generals and governments and everyday people practically since the invention of written language.
As we will see in this lesson, modern cryptographic techniques are essential to guaranteeing the security of our transactions on the Internet. Cryptography plays a role whenever you make an online purchase at Amazon or provide your password to Google. If we couldn't rely on those transactions being secure -- i.e., being encrypted using some cryptographic algorithm -- we wouldn't have the Internet as we know it today.
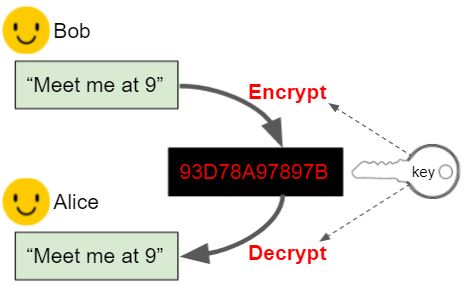
- perform frequency analyses to identify substitution and transposition ciphers
- encrypt and decrypt messages using Vigenere Cipher
- describe the key exchange problem
- explain how substitution ciphers can be broken
- use target vocabulary, such as frequency analysis, polyalphabetic substitution, one time pad, and key exchange problem while describing symmetric encryption ciphers, with the support of concept definitions and vocabulary notes from this lesson
6.6.2. Learning Activities¶
Let's take a look at some of the classical ciphers and some of the basic principles of cryptography. There are several hands-on activities in this lesson, where you'll have a chance to practice encrypting and decrypting messages and analyzing ciphers.
Part 1: Simple Substitution Cipher
Activity: Simple Substitution Cipher
(Open widget in separate window)
- By Hand. Use a simple substitution cipher to encrypt your name. Choose your own keyword to create a cipher alphabet. Then use the widget above to check your result.
- Decrypt. The following word, SIRTQSMTCKJ, was encrypted with the keyword simple. Can you decrypt it?
- Brute force attack. How many keys (arrangements of the alphabet) would you have to try to perform a brute force attack?
Part 2: Frequency Analysis
Activity: Frequency Analysis
(Open widget in separate window)
Frequency analysis. One of the following messages was encrypted using a substitution cipher and the other with a transposition cipher. Can you identify which is which? Paste the messages into the frequency analyzer tool (above) and observe their frequency histograms.
Text 1.nybfx ymjgj xytky nrjxn ybfxy mjbtw xytky nrjx nybfx ymjfl jtkbn xitrn ybfxy mjflj tkktt qnxms jxxn ybfxy mjjut hmtkg jqnjk nybfx ymjju thmtk nshwj izqny dnyb fxymj xjfxt stkqn lmyny bfxym jxjfx tstki fwpsj xxny bfxym jxuwn sltkm tujny bfxym jbnsy jwtki jxufn wbjm fijaj wdymn slgjk twjzx bjmfi stymn slgjk twjzx bjbj wjfqq ltnsl inwjh yytmj fajsb jbjwj fqqlt nslin wjhy ymjty mjwbf dnsxm twyym jujwn tibfx xtkfw qnpjy mjuwj xjsy ujwnt iymfy xtrjt knyxs tnxnj xyfzy mtwny njxns xnxyj itsny xgjn slwjh jnaji ktwlt titwk twjan qnsym jxzuj wqfyn ajijl wjjt khtru fwnxt stsqd
Text 2.
ttbti swhot istta osmwh gflhs tsecf liaho ondia henit ahena nwtpnf ewtie fpree rhbou hnhbo uerli deovw rlode oeasr hrdsa itrei ttein ittie ntote gceoo rrits etegc psoya hsfmt sesfm iahew dtseo oiewh pheet tecir uytss sohts ssoks isero oisen oeawa vtnee watne ewagn rtenw egnit htwih tpiao reeet eoaoo sieuo tiiei ieidg dfvih pliee omrol setet wtese iotao siaoo fwphe lwtof wtofs tsipt wtsid egfed gfweo gtaea grehn oeofl psrdm fssri sdbnv foone avefi nweoi arowg fiaef nsteb isefc tieag ieare ahgha hrdhy irsoi rseli ceeli ctryt ewskh nphst oahss nsrer oelur droan
Part 3: Vigenere Cipher
Activity: Vigenere Cipher
(Open widget in separate window)- By Hand. Use the Vigenere cipher to encrypt your name. Choose your own keyword.
- Decrypt the following message, which was encrypted using Vigenere Cipher, with the keyword zebras.
SLJJ IK OSMPADOLBSELHG
- Frequency Analysis. Use the Frequency Analyzer tool (above) to count the letter frequencies in the following text, which is the same text that was encrypted in an earlier exercise. In this case it was encrypted using Vigenere Cipher. What differences do you observe from the histograms you used in the previous exercise?
sabjt zdffj tgexj dekhx xrslg ixfrk ssgki edwj kwsrx ivayd sgnik csnzt ozwuy esfip wfgnp jjhfd wtzt ozwuy ewosd yoxai mzexh xxrsl gifgo ugsgz nuqie llasc jkws rxivs wzwpe oxhki kilve tkhwr ibjof njbik fdwt ztozw uyeko vjegg elpge asabj tzdaj etwqs gueko ejiw wgeev vwqcu yifff fwojd ytnez zhoft zhrhs exnvf lsod afies kphfi ffhji eusxp vandr xvwwq ibcly nmoxd aqidk tzds uyejv ezznk gsskt zdtfi igcab jsgee scicd xivpj dwfet hdvj fdlge ujoed sgztk msjji wrxbl tznvj kiwrm ojiks iefna swcv iffvf teaui ewojf spuoj essvv akmok hwryq vrdzx jmevd ksve gegpd psqmt fngmp z
Part 4: Perfect Secrecy and the Key Exchange Problem
6.6.3. Summary¶
In this lesson, you learned how to:
6.6.4. Still Curious¶
- Read more about the historical evolution of ciphers in Chapter 5 of Blown to Bits (pg. 166+)
- You can find more cryptography challenges at CryptoClub.org.
- Here is a crypto challenge game at Khan Academy.
- If you want an additional challenge, try creating an app that does Simple Substitution. It will be similar to the Caesar Cipher App you made in Unit 5. Or try incorporating an encryption scheme into one of your own apps.
6.6.5. Self-Check¶
Here is a table of some of the technical terms discussed in this lesson. Hover over the terms to review the definitions.
|
cipher
cryptography encryption plaintext ciphertext |
decryption
encryption key encryption algorithm symmetric encryption substitution cipher |
transposition cipher
brute force attack frequency analysis polyalphabetic substitution one time pad key exchange problem |
- decryption
- This is challenging, but rewarding! Decryption is actually the process of converting cipher text back into plain text. For example: khoor ----> hello
- frequency analysis
- That's right! Frequency analysis is the technique whereby you count the letters in the secret message. In English, the letter with the highest frequency is 'e'. By counting letter frequencies you can identify the shift that was used to encrypt the message. That is why the Caesar cipher is not a secure cipher.
- encryption
- This is challenging, but rewarding! Encryption is actually the process of converting plain text into cipher text. For example: hello ---->khoor
- cryptography analysis
- This is challenging, but rewarding!
Q-5: One technique that can be used to break a Caesar cipher is called _________________________.
Q-6:
Suppose that the following word, EAIWSQI, was encrypted with a Caesar cipher and when you do a frequency analysis you learn that the most frequent letter was 'i'. What is the secret word? Type your answer into the Textbox. (Make sure there are no extra spaces in your answer.)
- Symmetric
- This is part of the correct answer.
- Alphabetic
- This is challenging, but rewarding!
- Transposition
- This is challenging, but rewarding! Transposition ciphers rearrange the letters in the plaintext message. These ciphers do not do that.
- Substitution
- Yes this is part of the correct answer.
Q-7:
Caesar cipher, simple substitution cipher, and Vigener cipher are all examples of __________ ciphers.
- Uses the same alphabet over and over again
- This is challenging, but rewarding! This description would apply to simple substitution or Caesar cipher.
- Rearranges the plaintext alphabet using a keyword
- This is challenging, but rewarding! A cipher that rearranges the plaintext alphabet would be a simple substitution cipher, including Caesar cipher.
- Rearranges the letters in the message according to some rule
- This is challenging, but rewarding! A cipher that rearranges the letters in the message is known as a transposition cipher.
- Uses multiple alphabets
- That is correct. An example would be the Vigenere cipher, which uses a keyword to select several alphabets to use in encryption and decryption.
Q-8:
A polyalphabetic cipher is one that ______________.
- the problem swapping Alice's key for Bob's key.
- OK, so you didn’t get it right this time. Let’s look at this as an opportunity to learn. Try reviewing this. Alice and bob need to share the same key, not swap different keys.
- the problem of securely sharing a symmetric key between Alice and Bob.
- Yes. Alice and Bob need to share their symmetric key in order to send secret messages to each other. How can that be done without Eve getting it?
- the problem of securely sharing an asymmetric key.
- No. Asymmetric keys are used in Diffie-Hellman and RSA to exchange symmetric keys.
- the challenge of setting up an exchange system where cryptographic keys can be stored securely.
- OK, so you didn’t get it right this time. Let’s look at this as an opportunity to learn. Try reviewing this. There is no such effort. It would be a bad idea to store everyone's keys in something like a central bank.
Q-9:
The key exchange problem is ____
6.6.6. Reflection: For Your Portfolio¶
Answer the following portfolio reflection questions as directed by your instructor. Questions are also available in this Google Doc where you may use File/Make a Copy to make your own editable copy.