
4.10. Impacts of CS Privacy Explore Curricular Activity¶
Time Estimate: 135 minutes
4.10.1. Introduction and Goals¶
Like any computing innovation, mobile computing has both positive and negative impacts, including legal and ethical concerns. We need to reflect on these impacts in general. We also need to think about the impacts we will create as we build our own mobile apps. In this lesson, we will explore the following:
| |
 |
Learning Objectives: I will learn to
Language Objectives: I will be able to
|
4.10.2. Learning Activities¶
Careful, your data is being collected!
Computing innovations, such as smartphones, collect information and data from their users and then use that data to accomplish tasks. In some cases those tasks may be obvious and part of the intended purpose of the innovation. In other cases, those tasks might be less obvious or even hidden from us. Watch the video below which explains that our Personally Identifiable Information (PII) to be recorded and used.
Explore Curricular Activity: How Computing Innovations Use and Analyze Data
Activity - Part 1: Data Types and Data Collection
First, we need to understand the various types of data and how it is collected from us. Some examples of data types are integers, numbers, booleans, text, image, video, audio, and signals. Data can also infer these types, such as fingerprints, temperature, music, length, pictures, etc. Data is gathered by data collection devices (e.g., keyboards, sensors, cameras, etc.). Complete this Data Types and Data Collection Reference Sheet with some examples of your own and/or with your class. When you’re done, this document can be used as a reference sheet for the remainder of this lesson.
Activity - Part 2: Classifying Data
Earlier in the course you learned about what a computing innovation is and discussed some examples. You also learned about input and output. Now that you know what a computing innovation is and the kinds of data that can be collected, you can determine what data is collected by specific computing innovations. Using this Classifying Data worksheet, identify the data used by the listed computing innovations and then classify the data as input or output. When you are finished, compare your answers with a classmate.
How is your data being used and are you concerned? Disparate personal data, such as geolocation, cookies, and browsing history, can be aggregated to create knowledge about an individual. PII and other information stored online can be used to enhance a user’s online experiences and to simplify making online purchases. You may have seen targeted ads when browsing the web. Targeted ads are ads specific to you based on your browsing and purchase history. They are being used by stores (as shown in the NY times video below) and by websites for internet advertising.
Discussion: Watch the video to the below on Retailer's Predictions from the New York Times. (Here is the full article if you're interested in reading more.). Then, take a look at a receipt from Target and the data available on it. Consider the following questions to help you understand how companies like Target collect information on buying habits:
- What data is included on the receipt?
- How might this data reveal demographics, personal life details, and other information about the consumer?
- Is it different if you pay for purchases with cash vs a credit or debit card?
- Is it different if you purchase items in the brick-and-mortar store or the online store?
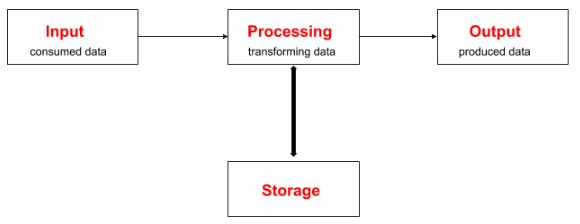
Input Process Output Storage: Computing innovations involve data which can be used in different ways. Some data is considered input while other data is considered output. An Input Processing Output Storage (IPOS) Structure Chart helps to classify data and see how that data is being used as input, then processed by a program to give an output to the user, and also how that data is stored.
Exercise: Can you draw, label, and explain the scenario of having to type a paper for a class using an IPOS structure chart?
Data Concerns
The collection of our data raises a variety of concerns involving data privacy, data security, and data storage. For example, commercial and governmental curation of information may be exploited if privacy and other protections are ignored. Having a website collect and remember your login information, for example, may be convenient because it saves you time, but it also comes with risks and concerns:
- Data Privacy - assures that personal information (and sometimes corporate confidential information as well) are collected, processed (used), protected and destroyed legally and fairly.
- Data Security - controls access to personal information and protects against its unauthorized use and acquisition.
- Data Storage - how you archive your data. The two types of storage are hard data (RAM, Hard Drive, flash drives, solid state) and remote data (cloud computing) - Techopedia
Activity - Part 3: Collecting Data
The About My Info website (aboutmyinfo.org) asks for personal data to determine how easily identifiable someone is from their data. Data such as this is often used by doctors and schools. Explore the About My Info website and then explore the privacy policy for your favorite social media site. As you explore, record your findings and answer the questions on the Collecting Data worksheet.
Activity - Part 4: Explore a Computing Innovation
Select a computing innovation and answer the following questions independently about your selected innovation:
- Identify the data used by the computing innovation.
- Write a paragraph that explains how the data is consumed, transformed, or produced by this computing innovation.
- Write a paragraph that explains any data privacy, security, or storage concerns related to the computing innovation.
Read Blown to Bits Chapter 2

Blown to Bits Chapter 2 focuses on the issue of how the digital explosion affects our privacy. This is an especially important issue for today's mobile computing generation. As we’ve seen, our smartphones and tablets can not only track our electronic correspondence, they can track our whereabouts, opening whole new areas of potential privacy infringements.
What's especially interesting about the privacy question is that, for the most part, many seem to be willing to trade privacy for convenience. We don't mind letting the supermarket track our purchases if that brings us discounts. And we don't seem to mind letting mobile apps know and record our whereabouts in exchange for some service we like like GPS directions or even games.
Read Chapter 2 of the updated Blown to Bits to learn about some of the ways our electronic devices impinge on our privacy — some of the stories will surely surprise you. As you read the chapter, complete a double entry journal sheet. Once you've completed the chapter, discuss your journal entries with your class. You might want to read through the portfolio homework questions below for some key ideas to focus on.
4.10.3. Summary¶
In this lesson, you learned how to:
4.10.4. Still Curious?¶
Read up on other ways that data is collected and used:
- Learn more about cookies and how they are used to track you on the websites you visit. This video from The Guardian also does a nice job explaining how cookies are used.
- Learn more about targeted web ads and adblockers.
- Learn more about voter data and what's private and public information. Here's an example of Minnesota's public voter list information and the US Election Project has information on all 50 states.
- Snapchat's new SnapMap feature is of concern to many parents of children who may not understand how their information is being used. Read more about SnapMap and the privacy concerns it raises from The Guardian and The Verge.
- Learn more about HIPAA by reading here and/or watching this video.
- Learn more about FERPA by reading here and/or watching this video.
4.10.5. Self-Check¶
|
Personally Identifiable Information (PII)
Cookies Data Privacy Data Security Data Storage |
4.10.6. Reflection: For Your Portfolio¶
Answer the following portfolio reflection questions as directed by your instructor. Questions are also available in this Google Doc where you may use File/Make a Copy to make your own editable copy.